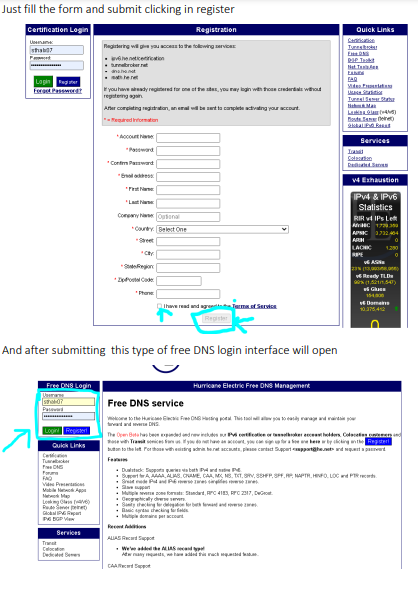
Online Free Hosting Guide Creating User Account Applicant Login Page: This is the homepage for applicants (before login). User can use the general services shown without registering in the system. For using rest of the services applicant has to create an account. Steps: • click on the browser. • Enter the URL in the address […]
Best Top Two WordPress Magazine Themes of 2021
WordPress CMS is the best platform for publishing articles news, blog, and views of any current issues. If you want to make a magazine website with WordPress, then you will need information code programming to provide you to best news blogs theme 2021. Publisher Theme Complete WordPress Theme for Magazine, Newspaper and Blog Sites. […]
How to Remove your card info From Facebook Account
How to Remove your card info From Facebook Account step 1 go to: https://www.facebook.com/ads/manager/account_settings/account_billing step2: go to card *****789 section and right click to … and remove the card info.
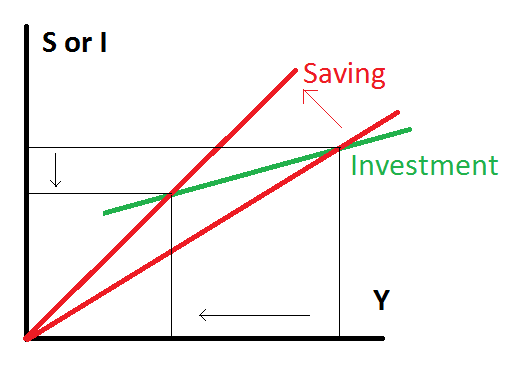
Paradox of Thrift
The term “Paradox of Thrift” refers to the situation where increase in savings ultimately reduces to productive capacity, employment and saving itself. J.M. Keynes introduced the concept of paradox of thrift while discussing the great depression of the 1930s. Thriftiness means the tendency of saving more. The classical economists regarded the saving as a […]
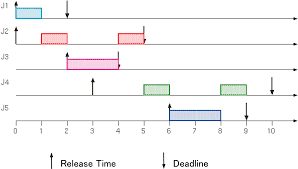
Calculate Effective Release Time and Effective Deadline
Effective release time • If a job has no predecessors, its effective release time is its release time • If it has predecessors, its effective release time is the maximum of its release time and the effective release times of its predecessors effective release time ri of job i = ri if i has no predecessors max{rj + e–j | j […]
Ransomware Virus Attack ? How it works | How to Be Safe From Ransomware
‘Ransomware’ is a type of malware that attempts to extort money from a computer user by infecting and taking control of the victim’s machine or the files or documents stored on it. • Typically, the ransomware will either ‘lock’ the computer to prevent normal usage, or encrypt the documents and files on it to prevent […]
What Is Bitcoin?
A medium of exchange that uses cryptography to secure transactions and control the creation of new units. What Is cryptography? Cryptography is the practice of transforming data or information into an unreadable format in order to increase security so that only those with a proper secret key can read the unencrypted information. What Is Bitcoin? […]
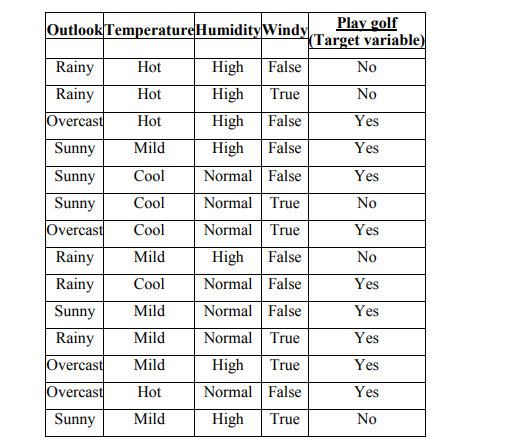
How best attribute is selected in a decision-tree? Select the root attribute of the decision-tree from given sample data.
How best attribute is selected in a decision tree? Select the root attribute of the decision tree from the given sample data. Solutions a) Entropy using the frequency table of one attribute: b) Entropy using the frequency table of two attributes: Information Gain: The information gain is based on the decrease in entropy after a […]
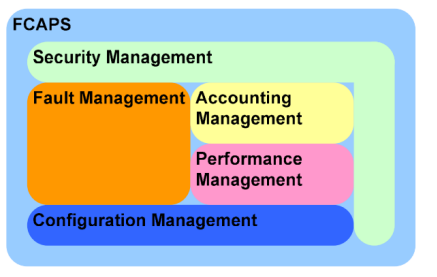
FCAPS (fault-management, configuration, accounting, performance, and security)
FCAPS categorizes the working objectives of network management into five levels. The five levels are fault-management (F), the configuration level (C), the accounting level (A), the performance level (P), and the security level (S). FCAPS is the ISO Telecommunications Management Network model and framework or network management. FCAPS is an acronym for fault, configuration, accounting, […]