Neural Network defines as real biological neural networks such as our brain or an artificial neural network simulated computer vision. Neural network either biological or simulated artificial that consist of a large number of simple data neurons that receive and transmit signals to each other. According to Dr Robert Hecht nielsen “a computer system made […]
Lists
What is object oriented DBMS?
object-oriented DBMS is derived from the model of the object-oriented programming view. representing both consistent data as stored in databases, as well as transient data, as found in executing programs.object-oriented DBMS use reusable elements known as an object.• Each object contains a data part and a set of operations that work upon the data. The object and […]
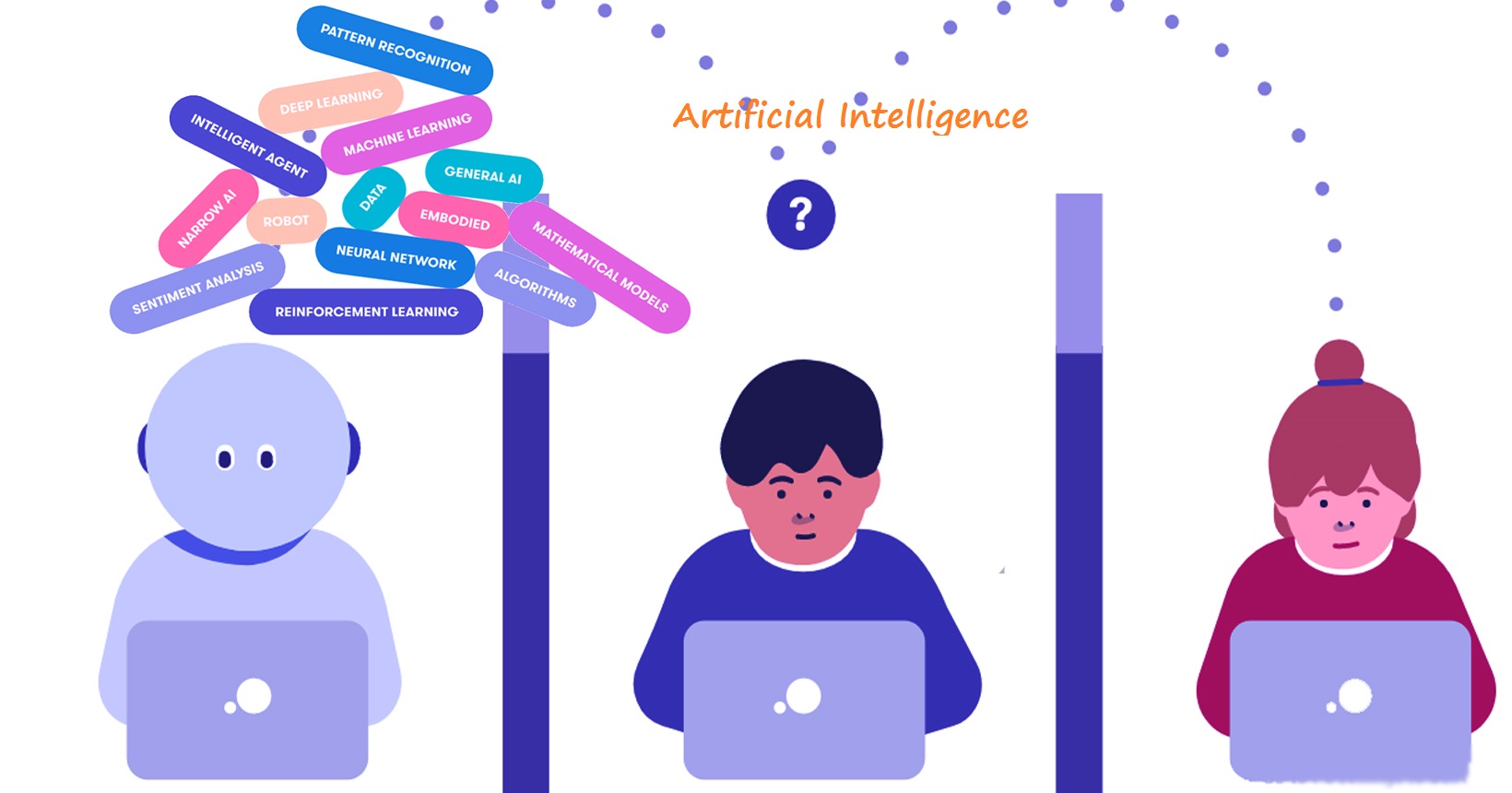
What is Artificial Intelligence?
Morden Branch of computer science the terminology “Artificial Intelligence” mostly uses an innovative solution. AI define as the ability to perform tasks in a complex environment without constant guidance by a human and the ability to improve performance by learning from experience. Every nature of the term “AI” asking the logical question where intelligent behavior […]
What is digital image processing?
Image-processing define as converting the continuous analog signal to a two-dimensional image as a finite set of digital values. That converted value also called a pixel. It is defined by the mathematical function f(x, y) where x and y are the two co-ordinates horizontally and vertically. The value of f(x, y) at any point is given the […]
What is authentication application?
Security is the main thing to keep our application robust and manage identically. Nowadays many application security is broken by national and international hackers. The Application used to authenticate a user known as authentication application. Mainly Authentication app implements two-step verification services using the Time-based One-time Password Algorithm. Today’s authenticator app is used in Web hosting […]
What is management information system?
Management + Information + System System: A set of interrelated parts that must work together to achieve a common goal Input Process Output Feedback/ control/ evaluation Information is meaningful data related to something Management: Is an art & science of getting things done by and through people Effectiveness (to achieve a goal) Efficiency – Utilization […]
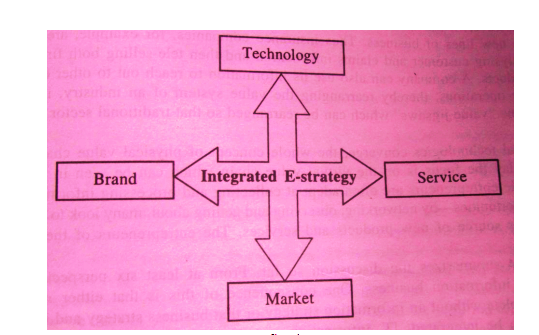
What do you understand by e-strategy?
The strategy is defined as a high-level plan to achieve one or more goals under certain and uncertain conditions. Strategy in online business is also referred to as e-strategy and it covers all aspects of marketing, public relations, advertising, media, strategic communication as well as online communication. The e-strategy for e-commerce emphasizes how the web […]
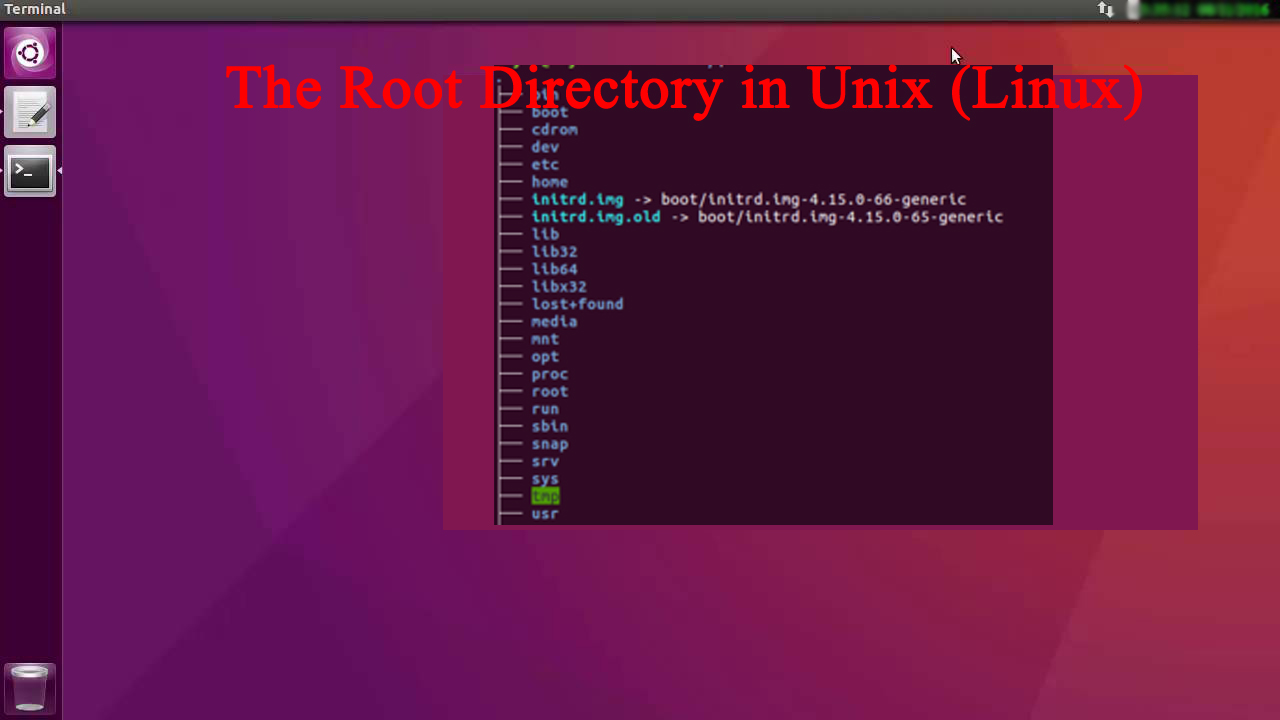
The Root Directory in Unix (Linux)
The root directory in UNIX ( Linux ) operating system all directories and subdirectories designated by a forward slash. Descriptions / The root directory, the top-level directory in the FHS. All other directories are subdirectories of root, which is always mounted on some partition. All directories that are not mounted on a separate partition are […]
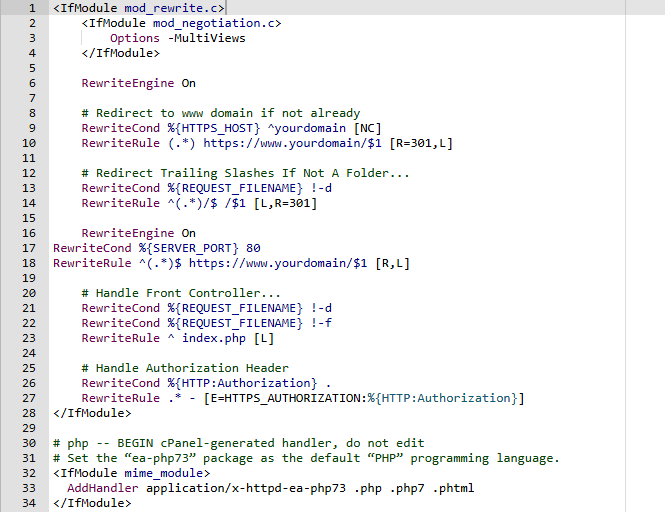
Redirect HTTP to HTTPS Using .htaccess
.htaccess file is used to the configure of file directory, URL redirection, access control. .htaccess file hidden in the control panel of the UNIX operating server. Redirect HTTP to HTTPS Using .htaccess Example code <IfModule mod_rewrite.c> <IfModule mod_negotiation.c> Options -MultiViews </IfModule> RewriteEngine On # Redirect to www domain if not already RewriteCond %{HTTPS_HOST} ^yourdomain [NC] RewriteRule […]