Security is the main thing to keep our application robust and manage identically. Nowadays many application security is broken by national and international hackers. The Application used to authenticate a user known as authentication application. Mainly Authentication app implements two-step verification services using the Time-based One-time Password Algorithm. Today’s authenticator app is used in Web hosting […]
Author: Code
How to Create Breaking Post with feature image on WordPress Site Code Example:
WordPress is a free and open-source content management system written in PHP and paired with a MySQL or MariaDB database. <?php $recent_posts = wp_get_recent_posts(array( ‘numberposts’ => 2, // Number of recent posts thumbnails to display ‘post_status’ => ‘publish’ // Show only the published posts )); foreach($recent_posts as $post) : ?> <center> <a href=”<?php echo get_permalink($post[‘ID’]) […]
What is management information system?
Management + Information + System System: A set of interrelated parts that must work together to achieve a common goal Input Process Output Feedback/ control/ evaluation Information is meaningful data related to something Management: Is an art & science of getting things done by and through people Effectiveness (to achieve a goal) Efficiency – Utilization […]
Why are algorithms so important in Programming?
Algorithms are the building blocks of computer programs. They are as important to programming as recipes are to cooking. Definition of algorithm An algorithm is a well-defined procedure that takes input and produces output. The analogy to a recipe is good here, since a cook will take ingredients (the input), mix things together and cook […]
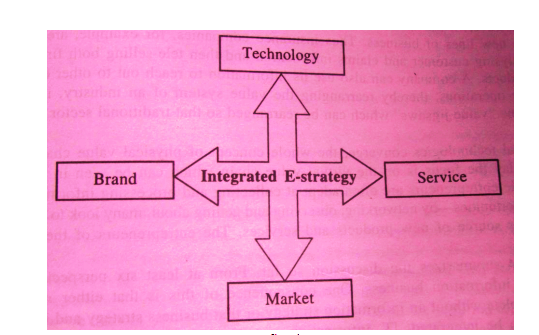
What do you understand by e-strategy?
The strategy is defined as a high-level plan to achieve one or more goals under certain and uncertain conditions. Strategy in online business is also referred to as e-strategy and it covers all aspects of marketing, public relations, advertising, media, strategic communication as well as online communication. The e-strategy for e-commerce emphasizes how the web […]
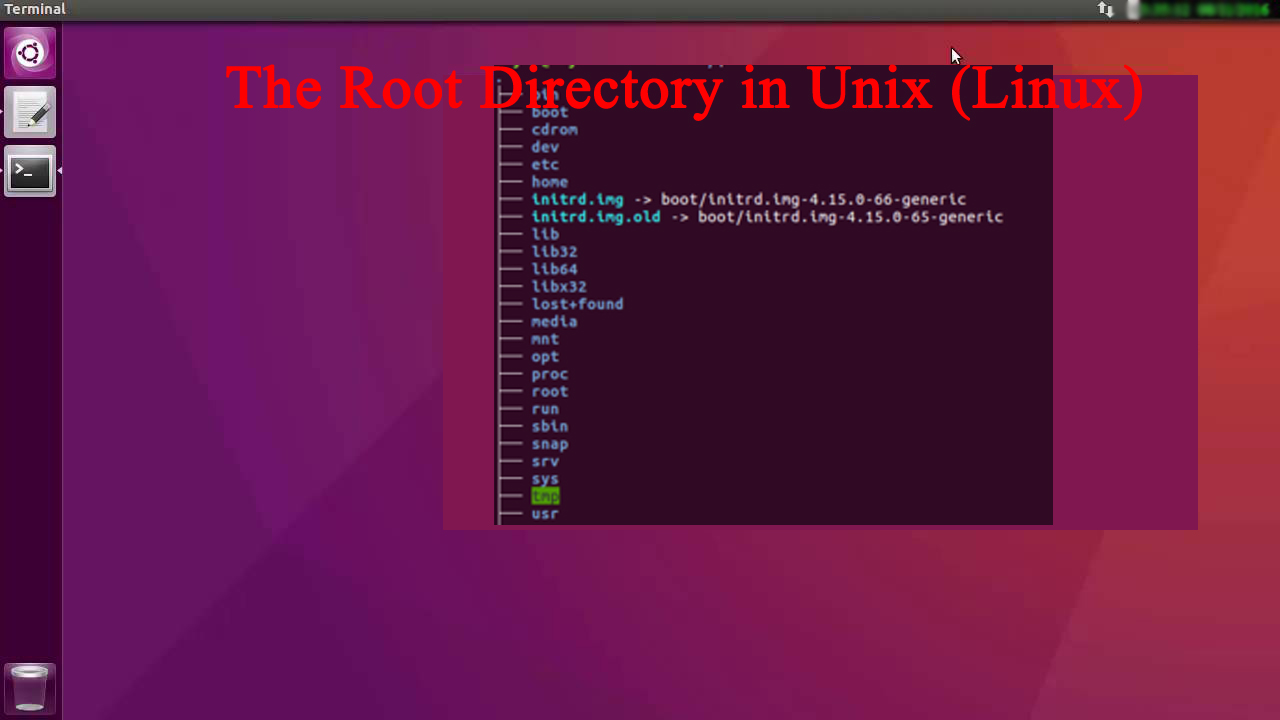
The Root Directory in Unix (Linux)
The root directory in UNIX ( Linux ) operating system all directories and subdirectories designated by a forward slash. Descriptions / The root directory, the top-level directory in the FHS. All other directories are subdirectories of root, which is always mounted on some partition. All directories that are not mounted on a separate partition are […]
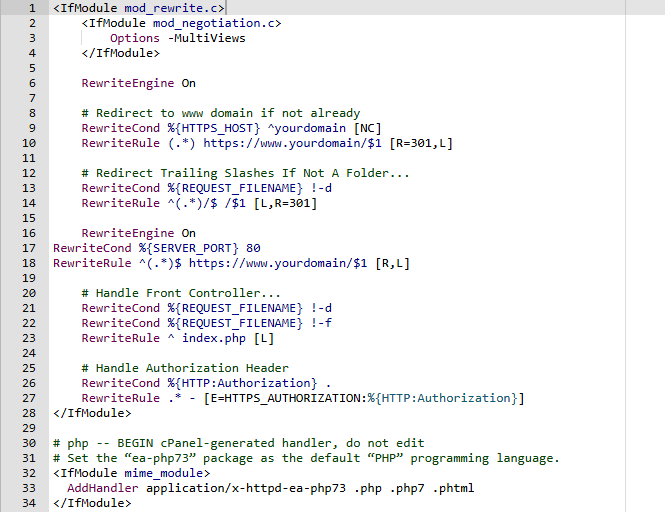
Redirect HTTP to HTTPS Using .htaccess
.htaccess file is used to the configure of file directory, URL redirection, access control. .htaccess file hidden in the control panel of the UNIX operating server. Redirect HTTP to HTTPS Using .htaccess Example code <IfModule mod_rewrite.c> <IfModule mod_negotiation.c> Options -MultiViews </IfModule> RewriteEngine On # Redirect to www domain if not already RewriteCond %{HTTPS_HOST} ^yourdomain [NC] RewriteRule […]
HTTP Status Code
Hypertext Transfer Protocol status codes are issued by Server response to their clients.Some of the Hypertext Transfer Protocol lists is mention below: Information Response Redirection messages Client error responses Server error responses Descriptions CODE MESSAGE 200 ok 204 No Content 2. Redirection messages 301 Moved Permanently 302 Found / Moved Temporarily 304 Not Modified 307 Temporary […]
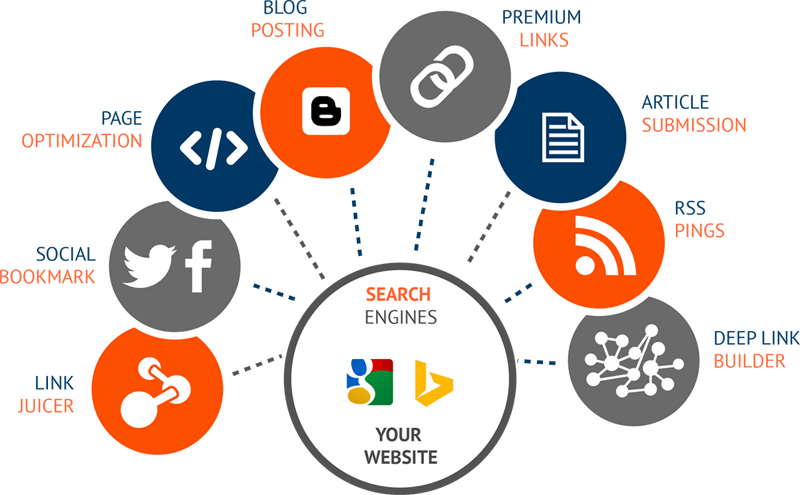
What is Search Engine Optimization (SEO) and How It Work?
Generally, Search Engine Optimization is the technique of Marketing which can support to derive real customer on their products or services. Search Engine Optimization defines the process of optimizing Webpages, information services, products, portfolios using the internet. SEO can be categories into two categories which are Local SEO: Search Engine Optimization which is allocated on […]